Windows Kernel Patch Protection
- Windows Kernel Patch Protection Disable
- Windows 10 Kernel
- Windows Kernel Patch Protection
- Kernel Patch History
- Apply Kernel Patch
Microsoft's September 'Patch Tuesday' updates are now available. These updates focus on bug fixes and improvements for several Windows 10 releases. Notably, the update for Windows 10 May 2019. English: the cause of the problem is your pirated copy of Windows 7 which has the kernel patched. Use BCDEDIT.exe command to confirm you have xNtKrnl.exe set as.
If you receive a Kernel Security Check FailureStop Error or Blue Screen on Windows 10/8/7, then this post has some troubleshooting steps you may want to try out. This error is usually caused due to Memory or Driver incompatibility issues or corruption of system data.
Kernel Security Check Failure
If you face this issue, here are a few things you may want to try. See which applies to your system and proceed with those suggestions.
1] First, install all the latest available Windows Updates and scan your computer with you antivirus software. You may want to also run System File Checker to replace corrupted system files, if any. You may want to also physically ensure that your RAM, Hard Disk, and other hardware components and accessories are connected properly.
2] Boot in Safe Mode or Clean Boot State and see if the problem disappears. If the problem does not occur then it you will have to identify the offending program or driver and uninstall it.
3] Run the Driver Verifier Manager to check for corrupt drivers. If need be uninstall and reinstall or update the drivers.
4] Windows 10 has a Memory Diagnostic Tool which you can use to check for possible memory problems, including testing of the Random Access Memory (RAM) on your computer. Run it and see if it throws up any issues.
5] Scan your Hard Disk for errors. To run Check Disk on your System Drive (C), type the following in CMD and hit Enter:
If required, restart your computer.
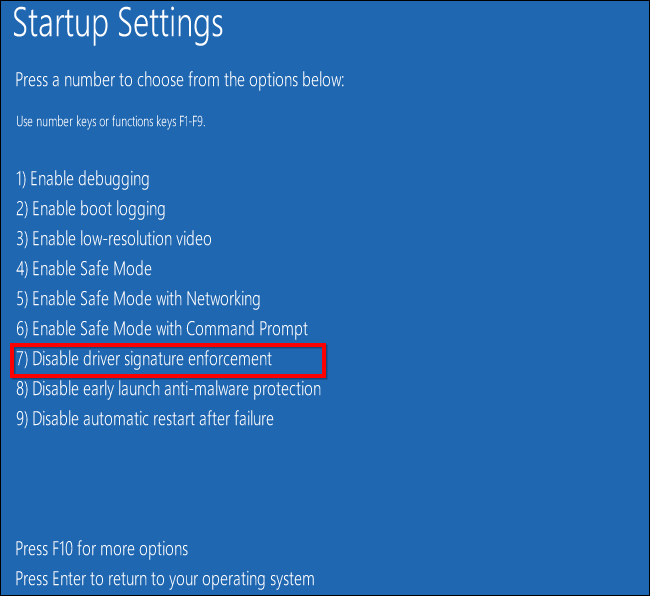
6] If you cannot log in to your Windows computer, boot into Advanced Startup Options and open an elevated command prompt window. The process is explained there in detail.
Once at that screen, select Troubleshoot > Advanced options > Command Prompt. Using the CMD, you can access the more advanced built-in Windows tools easily.
If you wish to directly access these Advanced startup options when working on your Windows 10, you can do so via the Settings app of Windows 10 > Update & Security > Recovery > Advanced startup and click the Restart now button.
Now you will have to enable the Legacy Boot Policy. Type the following command and hit Enter:
Now you will be able to log into you Windows desktop or Safe Mode to carry out the troubleshooting suggestions mentioned above.
All the best!
See this post if you receive a Critical Process Died error in Windows 10.
Related Posts:
Here's some bad news for Windows users. Microsoft's latest patch to protect Windows users from the Meltdown and Spectre chip vulnerabilities was found to be incompatible with various types of anti-virus software.
The worst part is this, users with non-compliant antivirus software will not be able to install any Windows security updates at all unless the software makers tweak their software or the user uninstalls the software completely.
It's a double whammy of sorts, leaving Windows users with either crippled security software or no protection against Meltdown. Yikes.
Microsoft's Meltdown patch
During Microsoft's testing of its latest January Windows patch, the company found that some antivirus programs are making 'unsupported calls into Windows kernel memory,' which can cause dreaded Blue Screen of Death (BSOD) errors when the patch is applied.
Even worse, some Windows machines are even rendered unbootable when the patch conflicts with affected antivirus programs that integrate deeper into a Windows machine's kernel.
Here's what's causing this issue. Since the Meltdown patch separates the kernel's memory from user processes completely, antivirus programs that violate Windows' built-in rootkit protection aka Kernel Patch Protection are causing Blue Screen of Death errors and endless reboot loops.
This means some Windows antivirus programs are going beyond what they're supposed to access (i.e, protected areas of the kernel). Since the patch stops this access, the affected antivirus programs themselves are now causing errors in Windows.
Note: A kernel is a very integral part of an operating system considering it has complete control over it, connecting software to various parts of a computer.
Microsoft's 'solution'
To prevent these errors, which can render certain Windows machines unbootable, Microsoft will not push nor install security updates to computers that have the affected antivirus software installed.
Antivirus makers will have to test their software to make sure that it's compatible with the Meltdown patch then update it with a specific Windows registry key. Once these steps are done, the Meltdown security updates can then be installed.
The company also said that this will be the new rule moving forward. Computers with antivirus software that do not have this registry key set won't be able to get security updates at all..ever. Asterix and obelix pdf.
This leaves users with these options. Either uninstall non-complying antivirus software completely or your machine will not be able to install security updates. Well, for most users, the choice is pretty clear-cut. You don't really want your machine to NOT have the latest patches.
Windows Kernel Patch Protection Disable
Antivirus makers are left with no choice
Microsoft said that it is working with antivirus makers to resolve this issue but there's a problem. While some developers are complying, other antivirus programs will completely break since they rely on kernel access to even function. Denying them this access will require a complete rewriting of the software.
Antivirus software companies who have complied with Microsoft's requirements include AVG, Avast, Avira, Bitdefender, ESET, Kaspersky, Malwarebytes, Sophos, and Symantec.
Windows 10 Kernel
McAfee, Trend Micro and Webroot are also working to tweak their software for compatibility soon.
Next-generation security providers like Palo Alto Networks, FireEye, Cylance, and CrowdStrike claim that their software has been tested to be compatible but they are not willing to set the registry key required.
Companies that have yet to confirm compatibility nor set the registry key include 360, VIPRE, and Countertack.
Windows Kernel Patch Protection
For the status of antivirus companies' compliance with Microsoft's Meltdown patch requirements, click here.
Grab these new Apple updates now to protect you from the Spectre chip flaw!
Kernel Patch History
How about Apple products? What is the company doing to protect its products? Click here to read more about it.
Get security alerts as they happen.Apply Kernel Patch
Stay ahead of breaches, recalls, frauds and scams with Kim's Alerts newsletter.